Bastille Networks
Cellular & RF Threat Remediation
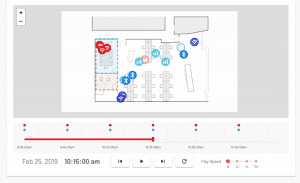
Bastille’s real-time Cellular, Bluetooth, BLE and Wi-Fi detection and location system locates all authorized and unauthorized devices within a campus or forward deployed location. Bastille accurately places dots on a floor-plan for device location and sends alerts when a device is found where it should not be or doing what it should not do.
Discover
The core and multi-patented technology of our sensor arrays and analytics continuously scans your airspace and detect wireless emitters, digitally demodulate those signals, identify protocols and individual unique devices. This allows Bastille to put an accurate dot on a floor plan map of your facility to show the location of each individual device.

Anaylyze
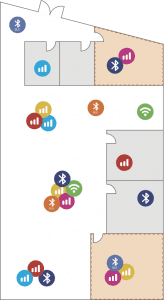
Bastille provides context information about the devices it locates. This allows you to tell whether the device that is represented by the dot is connected with other devices, what kind of data it’s streaming, or if it’s being actively attacked in certain cases.
Rule-based alerts can be established that interact with your incident response workflow. Using integrations, Bastille alerts can be used to send emails, text message phone calls, or to instantiate tickets in an external incident response system like PagerDuty, ServiceNow, or Lenel OnGuard.

Act
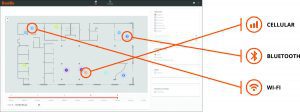
You can undertake various levels of investigation. For example, if you click through a Bluetooth device, Bastille might be able to tell you that it’s a Sony device and give you a model number that corresponds to a television. With that information, you might infer that somebody has just put a television in your space and it has an active Bluetooth connection. From there, you may choose to physically intervene to remove the device, or decide to use one of the Bastille integrations to your other network systems to disable the device automatically.
Similarly, you can use Bastille’s DVR feature to go back in time and see a given device’s presence and location history. Through this forensic analysis, it may become clear that the device has been in or near restricted areas, or that the device has been present during off-business hours in a way that is indicative of involvement in a malicious event.